
The EU’s Cyber Resilience Act (CRA) marks a turning point in the way digital products are secured across Europe. By 2027, all software will need to comply with CRA requirements, and as early as next year, companies will face mandatory cybersecurity incident reporting.
This issue is particularly critical for the energy sector, where outdated and poorly secured systems are still in use. A lack of proper safeguards can lead to severe consequences – not only financial but also operational and social.
- CRA applies to all software in the EU starting in 2027.
- For the energy sector, this means obligations such as SBOM, secure-by-design, and incident reporting.
- TTMS supports companies in preparing for and implementing CRA requirements.
- Ignoring the regulation may result in fines, market exclusion, and exposure to real cyberattacks.
1. Why is the energy sector especially vulnerable?
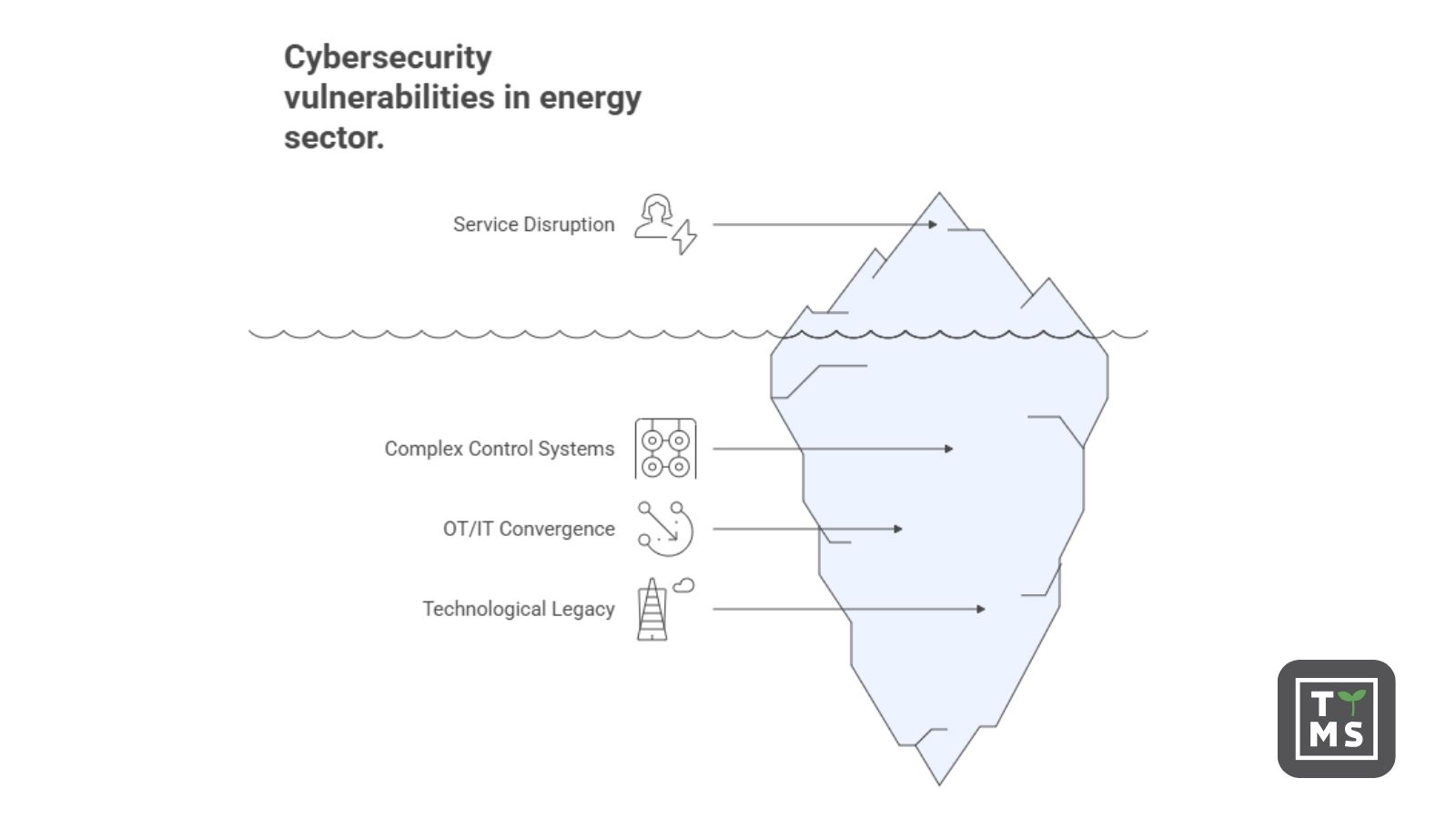
The energy sector is the backbone of modern society – the economy, public administration, and daily life all depend on its stability. As critical infrastructure, electricity supply must be uninterrupted. Any disruption can cause serious social and economic fallout – from halting transport and communications to crippling hospitals or emergency services.
Yet, this infrastructure relies on complex control systems such as SCADA, RTU, EMS, or HMI. Many of them were designed in an era when cybersecurity was not a top design priority. Built primarily for performance and reliability, they are often ill-equipped to withstand today’s digital threats.
The challenge intensifies with the convergence of OT and IT systems. More elements of physical infrastructure are now connected to corporate networks, increasing the attack surface and complicating risk management. Cybercriminals no longer need physical access to a power plant or substation – a single vulnerability in a remote-control system may be enough.
Adding to the risk is technological legacy. Many organisations still rely on outdated operating systems and applications deeply embedded in technological processes. These cannot be easily updated or replaced, making them an easy target for cyberattacks.
1.1 The threat is not theoretical – real incidents prove it.
In 2017, a cyberattack targeted the German company Netcom BW, a telecommunications network operator owned by EnBW, one of Germany’s largest energy providers. The attacker was a Russian national and a member of Berserk Bear, a group linked to Russia’s FSB intelligence service. The goal was to infiltrate communication infrastructure used not only by Netcom BW but also by energy system operators. While the companies assured that the core energy infrastructure remained intact, the attack exposed vulnerabilities in the supply chain and the dependencies between IT systems and critical energy assets.
This is a warning that cannot be ignored. Incidents like this highlight that cybersecurity cannot stop at the boundaries of a power plant or transmission grid – it must extend to technology suppliers, communication systems, and all interconnected digital components. This is precisely why the implementation of the EU’s Cyber Resilience Act is not only a legal requirement but also a strategic step towards building a resilient energy sector for the future.
2. CRA – What Does It Mean for Energy Companies and How Can TTMS Help?
The new EU regulation introduced by the Cyber Resilience Act (CRA) imposes binding cybersecurity obligations on software providers across the energy sector. For many organisations, this means reorganising development processes, implementing new tools, and ensuring both formal and technical compliance. This is where Transition Technologies MS steps in, offering both advisory and technological support.
2.1 Mandatory SBOMs (Software Bill of Materials)
CRA requires every company delivering software to maintain a complete list of components, libraries, and dependencies used in their product.
How TTMS helps:
We implement tools that automate the creation and updating of SBOMs in popular formats (e.g. SPDX, CycloneDX), integrating them with CI/CD pipelines. We also support risk analysis of open-source components and help establish dependency management policies.
2.2 Secure-by-Design Development
CRA enforces the obligation to embed security into products from the very first design stage.
How TTMS helps:
We provide threat modelling workshops, application architecture security audits, and the implementation of secure DevSecOps practices. Our support also includes penetration testing and code reviews at every stage of the product lifecycle.
2.3 Vulnerability Management
The regulation requires organisations to detect, classify, and patch vulnerabilities quickly – not only in their own code but also in third-party components.
How TTMS helps:
We build and integrate vulnerability management processes – from static scanning (SAST) and dynamic testing (DAST) to real-time vulnerability monitoring systems. We help implement procedures aligned with best practices (e.g. CVSS, CVD).
2.4 Incident Reporting
Every major security incident must be reported to ENISA or the local CSIRT within 24 hours.
How TTMS helps:
We create incident response plans (IRPs), implement detection and automated reporting systems, and train IT and OT teams in CRA-compliant procedures. TTMS can also act as an external cyber emergency response partner.
2.5 EU Declaration of Conformity
Software providers must deliver a formal document confirming compliance with CRA requirements – this is not only a declaration but also a legal responsibility.
How TTMS helps:
We support companies in creating and maintaining CRA-required documentation, including declarations of conformity, security policies, and technical support plans. We provide pre-implementation audits and assistance in preparing for regulatory inspections.
2.6 Additional Support and Parallel Development
Implementing CRA requirements does not have to mean halting other development projects. At TTMS, we provide additional resources in a staff augmentation model, enabling organisations to continue software development in parallel with the process of adapting applications to new regulations. This way, energy companies can maintain their pace of innovation while effectively meeting legal requirements.
Moreover, we offer comprehensive cybersecurity testing support across three key areas:
- Infrastructure audits and penetration testing
- Application audits and penetration testing
- Source code audits
All these services are delivered by TTMS in cooperation with Transition Technologies Software (TTSW), ensuring complete security both at the system and application level.
Why Work with TTMS?
- Proven experience in the energy sector – deep knowledge of SCADA, EMS, DMS, and OT/IT environments.
- Dedicated Quality and Cybersecurity experts – supporting organisations throughout the entire CRA compliance cycle.
- Ready-to-use solutions and tools – from SBOM management to incident response and risk analysis.
- Security-as-a-Service – flexible support models tailored to client needs.
3. Ignoring CRA Could Cost More Than You Think
Non-compliance with the Cyber Resilience Act is not just a formal issue – it is a real risk to business continuity and market presence in the EU. CRA foresees severe financial penalties – up to €15 million or 2.5% of global annual turnover – for failing to meet software security requirements. In addition, non-compliant products may be completely excluded from the EU market, which for many companies – especially those in critical infrastructure – could mean the loss of key contracts.
Neglecting security also increases the risk of real cyberattacks that may paralyse systems, leak sensitive data, and cause massive financial and reputational losses. A notable example is the ransomware attack on the Norwegian company Norsk Hydro in March 2019. The global aluminium producer and energy provider had its IT systems worldwide shut down, forcing plants to switch to manual operations. The direct and indirect costs exceeded $70 million, and the company struggled for weeks to restore operations and rebuild market trust.
Although this case dates back a few years, the number of similar attacks has been rising steadily amid Europe’s ongoing hybrid warfare. In 2025, Poland reported two major cybersecurity incidents in public institutions – one involving a personal data breach caused by an email system intrusion, and another targeting industrial control systems.
Cases like these show that failing to act proactively on cybersecurity can cost far more than investing in CRA compliance. It is not only a legal obligation but also a condition for maintaining competitiveness and business resilience in the digital era.

4. Cyber Resilience Act – Consequences of Non-Compliance and Real Risks of Cyberattacks
Failure to comply with CRA can result in:
- Financial penalties of up to €15 million or 2.5% of global annual turnover
- Exclusion from the EU market
- Increased risk of cyberattacks leading to system paralysis and massive financial losses
4.1 When Should You Start Acting? The Clock Is Ticking
The Cyber Resilience Act was adopted in October 2024. While full compliance will not be required until December 2027, one of the key obligations – reporting security incidents within 24 hours – will already apply from September 2026.
This means that companies – especially those in critical infrastructure sectors such as energy – have less than a year to prepare procedures, train teams, implement the right tools, and test their systems. Implementing CRA is not about a single document – it requires a comprehensive change in how software is developed and maintained, covering security, documentation, vulnerability management, and formal compliance.
Leaving compliance until the last minute is a recipe for errors, system gaps, and costly consequences. Organisations that start preparing now will gain not only a time advantage but also a strategic one, demonstrating to partners and customers that they take cybersecurity seriously – before being forced to.
This is precisely where Transition Technologies MS (TTMS) can make the difference. Our expert teams support organisations at every stage of CRA readiness – from analysing current processes and conducting security audits, to implementing SBOM and vulnerability management tools, developing incident reporting procedures, and preparing formal compliance documentation.
TTMS does more than advise – we implement real technical solutions, deliver training, and provide ongoing support as part of a long-term partnership.
If your organisation operates in the energy sector, do not delay CRA compliance – the consequences of inaction can be severe both operationally and financially. Talk to one of our cybersecurity experts and discover how TTMS can help you navigate this process smoothly and effectively. Visit ttms.pl/energy to learn more about the software and solutions we build for energy companies.
Looking for a quick summary?
Check out our FAQ section, where we have gathered the most important questions and answers from this article.
When does the Cyber Resilience Act (CRA) come into force and what is the timeline?
The Cyber Resilience Act was officially adopted in October 2024. Full compliance with its provisions will be mandatory from December 2027. However, from September 2026, companies will already be required to report security incidents within 24 hours. This leaves limited time for organisations to analyse, prepare, and implement the necessary processes – especially in the energy sector, where action must be both fast and methodical.
Which products and systems in the energy sector are covered by CRA?
The regulation applies to all “products with digital elements,” meaning both physical devices and software that can connect to a network. In practice, this includes critical energy management and control systems such as SCADA, RTU, EMS, DMS, and HMI – the backbone of digital energy infrastructure. If your software operates in this environment, CRA directly affects your organisation.
What specific obligations does CRA impose on energy companies?
Energy companies must introduce Software Bills of Materials (SBOMs), design systems with a secure-by-design approach, manage and patch vulnerabilities quickly, report major incidents to relevant institutions within strict deadlines, and prepare an EU Declaration of Conformity for their products. These are not mere formalities – they have a tangible impact on the security and resilience of entire energy systems.
What are the risks for companies that ignore CRA requirements?
Non-compliance may result in fines of up to €15 million or 2.5% of a company’s global annual turnover – whichever is higher. In addition, non-compliant products may be removed from the EU market entirely. Beyond financial penalties, ignoring CRA also exposes companies to real cyber risks, such as ransomware attacks. The Norsk Hydro case showed how a single incident can cause operational paralysis, data loss, and reputational damage with long-term consequences.
Does every company have to report incidents, even if there was no service disruption?
Yes. CRA requires reporting of any major security incident or actively exploited vulnerability within 24 hours of detection. A follow-up report must then be submitted within 72 hours, and a final summary within 14 days. This applies not only to incidents that cause outages but also to those that could potentially affect product or user security. The aim is to ensure early transparency and rapid mitigation across the entire EU market.